How to Master AWS Security in 2026 - Without chasing services or certs
Use This Step by Step Roadmap To Master AWS Security In 2026
If you ask most people how they’re “learning AWS security,” the answer usually sounds like this:
“I’m studying a bit of IAM, then some GuardDuty, then I might do the Security Specialty… or maybe Terraform next?”
This is exactly the problem.
In 2026, AWS security is no longer about knowing lots of services. It’s about understanding how security actually emerges from architecture, identity, and workload design.
Yet many professionals are still jumping randomly from service to service, or collecting certifications without ever building a mental model of how AWS fits together.
In this article I want to give you a step by step roadmap to actually master AWS security instead of memorizing the names of services.
The Biggest Mistake: Random Learning and Cert Collecting
The most common mistakes I see when people starting learning AWS security are:
Jumping from services like GuardDuty to WAF to Macie without context
Memorizing features instead of understanding why they exist
Treating certifications as the learning goal instead of a checkpoint
Never building anything hands-on
Skipping fundamentals like IAM and VPC design
In 2026, this approach is career-limiting.
Why?
Because organizations no longer need people who can list security services. They need people who can design secure cloud systems, explain trade-offs, and prevent incidents before tools start firing alerts.
Mastery starts with a learning roadmap, not a shopping list of services.
Step 1: Start With a Free Tier AWS Account (Yes, Really)
Everything begins with a real AWS environment.
Not diagrams. Not labs someone else built. Not theory.
Create a free tier account in Amazon Web Services and treat it like a production environment you are responsible for securing.
This immediately forces you to learn:
Root account protection
MFA configuration
Billing alerts and cost controls
The shared responsibility model
These aren’t “beginner topics.” They’re the first places real-world breaches happen.
If you can’t confidently secure a brand-new AWS account, nothing else matters.
Step 2: Master IAM Before Anything Else
IAM is the single most important AWS security domain in 2026.
Before touching any advanced service, you should deeply understand:
Users vs roles vs groups
Policies and policy evaluation logic
Explicit deny vs implicit deny
Service roles vs cross-account roles
Least privilege design (not theoretical — practical)
Many people think they know IAM because they passed an exam. Very few can:
Explain why a permission was denied
Design a role trust policy correctly on the first try
Model blast radius if credentials are compromised
Spend time breaking IAM on purpose in your lab. Create overly permissive roles, then fix them. Try cross-account access. Observe CloudTrail logs when permissions fail.
IAM is not just a service — it is the control plane of AWS security and it effectively defines the blast radius of your attacks.
Step 3: Build a VPC and Understand Network Security
Next, design your own VPC from scratch.
Not using a wizard. Not copying a blog post blindly.
Learn how:
Subnets actually isolate resources
Route tables control traffic flow
Security groups differ from NACLs
Internet Gateways and NAT Gateways affect exposure
Then ask security questions:
Which resources truly need internet access?
What happens if this subnet is compromised?
How does east-west traffic flow inside the VPC?
If you can’t diagram your VPC and explain its threat model, you’re not ready for advanced security tooling yet.
Step 4: Deploy a Real Workload (This Is Where Security Becomes Real)
Now deploy something realistic:
A simple web application
An EC2 instance or container
An RDS database or S3-backed workload
Once deployed, secure it progressively:
IAM roles instead of static credentials
Security groups tightened over time
Encryption at rest and in transit
Logging enabled by default
This step changes everything.
You stop thinking in terms of “services” and start thinking in terms of attack paths:
How would an attacker move from the app to the database?
What logs would prove it happened?
Which control would stop it?
This is the mindset AWS security roles demand in 2026.
Step 5: Add AWS Security Services With Context
Only now does it make sense to introduce services like:
GuardDuty
Security Hub
AWS Config
WAF and Shield
Because now you understand why they exist.
Instead of asking
“What does GuardDuty do?”
You ask:
“Which threats do I expect in this architecture?”
That shift — from tool-first to architecture-first — is what separates senior cloud security engineers from everyone else.
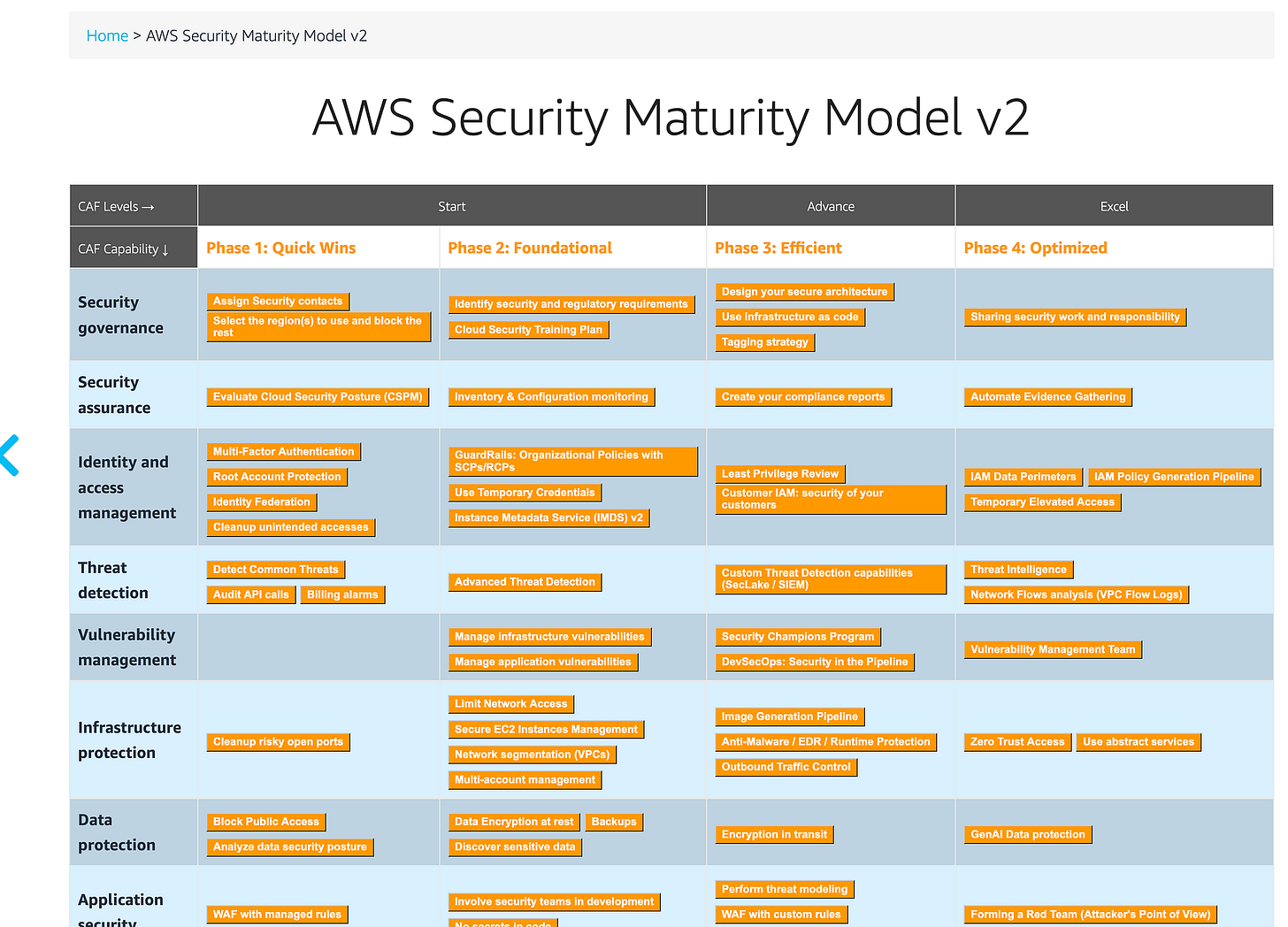
Using the AWS Security Maturity Model To improve over time
The AWS Security Maturity Model v2 exists for one reason: prioritization.
Unlike documentation — which shows all possible paths — this model focuses on:
Controls that are easy and cost-efficient to implement
Actions with the highest immediate security impact
A phased journey rather than an all-at-once approach
This is critical in 2026, where security failures are often organizational — not technical.
Think of the maturity model as your security backlog:
Early phases: MFA, logging, identity hygiene, account structure
Middle phases: detection, monitoring, policy enforcement
Later phases: automation, response maturity, governance at scale
You don’t “complete” the model. You progress through it intentionally.
Startups may only need the first phases.
Enterprises may assess alignment across the entire model.
Individuals learning AWS only need the fundamentals — but the right fundamentals.
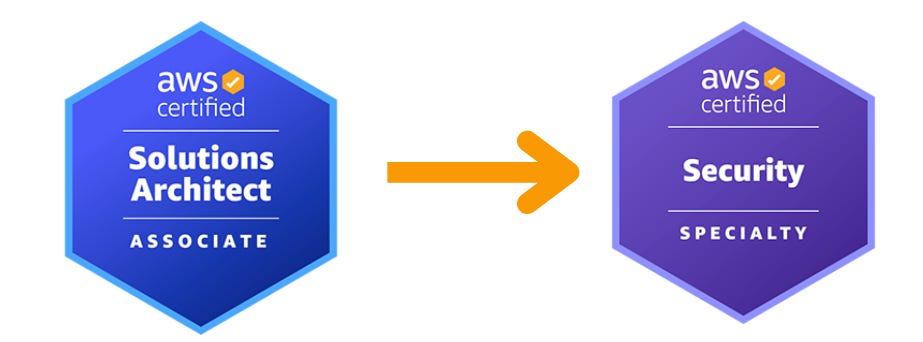
Certifications: Sequence Them to Match Maturity
Certifications still matter — but only when aligned with real learning.
If you are starting out then a strong, realistic path is:
Start with AWS Solutions Architect — Associate: Learn how AWS systems are designed and why trade-offs exist.
Then move onto AWS Security — Specialty: Validate deep understanding of IAM, logging, detection, governance, and secure architectures.
This mirrors how AWS itself expects security capability to mature — from architecture first, then specialization.
Certs should validate experience, not replace it.
What AWS Security Mastery Looks Like in 2026
By 2026, mastering AWS security means you can:
Design secure architectures from first principles
Prioritize controls using the Security Maturity Model
Explain security decisions in business terms
Improve posture incrementally instead of chasing perfection
It’s no longer about knowing every service.
It’s about understanding how security emerges from architecture, identity, and disciplined execution.
Final Thought
If you take one lesson from this roadmap, make it this:
AWS security mastery is not about speed — it’s about sequence
Build the foundations with IAM and VPC
Deploy a workload and secure it
Use the maturity model to prioritize.
Do that, and your AWS security skills will still be relevant long after 2026.



Really solid breakdown here.The mental model shift from "what tools do I know" to "what attack paths exist" is what seperates junior and senior roles in practice. I've seen so many poeple try jumping straight to GuardDuty or WAF without understanding why a misconfigured IAM role even matters, and then they get stuck when something breaks in prod. Starting with a real workload instead of theory makes those tradeoffs way more obvious.
Appreciate the emphasis on structural understanding over memorization.
Do you see parallels between building mental models here and how we frame systemic reasoning?