Agentic AI Will Change The Way We Use Cybersecurity Tools
The End of Cybersecurity Tools? How Agentic AI Will Change Everything
For years, cybersecurity vendors have sold us tools built on one core assumption:
Humans are the center of the security universe.
Humans write detection rules. Humans trigger investigations. Humans perform pen-tests. Humans correlate logs. Humans approve code reviews.
But AWS just proved that this era is ending.
At re:Invent, AWS announced a new class of frontier agents — autonomous AI agents capable of performing secure code reviews, architecture analysis, penetration testing, threat hunting, log correlation, incident investigation, and root-cause analysis without human involvement.
This is not another Copilot. This is not a chatbot.
This is a security engineer… as software.
And this changes everything.
The Problem: Cybersecurity Tools Weren’t Built for Agentic AI
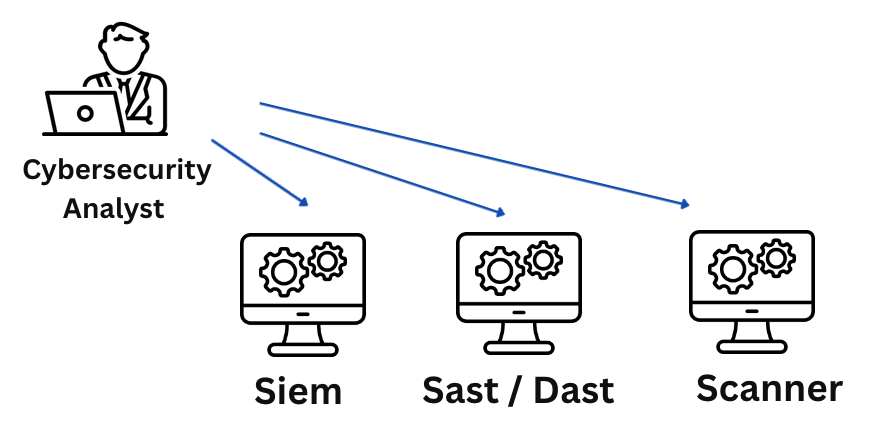
Look at almost any security product today, and you’ll see the same design philosophy:
SIEMs depend on humans to interpret alerts.
Scanners produce reports someone manually analyzes and prioritizes.
Pen-testing is periodic, performed yearly or quarterly.
Cloud security tools expect human-driven workflows via Jira or Slack.
Incident response remains too slow, bottlenecked by humans gathering evidence.
While automation lessened that load .. the entire cybersecurity stack was built for a world where human labor was the limiting factor and with a heavy reliance on tools
Agentic AI removes that bottleneck — and that means the assumptions behind most security tools no longer hold.
The new world we might be interacting with cybersecurity agents a lot more than cybersecurity tools
AWS didn’t just release a few AI features; it exposed a foundational shift in how security will operate.
The AWS Frontier Agent Explosion
AWS unveiled two new agentic AI systems that signal the end of manual, tool-driven cybersecurity.
And each one disrupts a category of tools we rely on today.
1. AWS Security Agent — the Autonomous Security Engineer
This agent can:
read architecture designs
perform secure code review
execute on-demand penetration tests
generate remediation code
validate your security baselines
run autonomously for hours or days
This single agent represents a seismic shift. It replaces:
static SAST tools
DAST tools
SCA tools
pipeline scanners
portions of AppSec teams
parts of manual code review
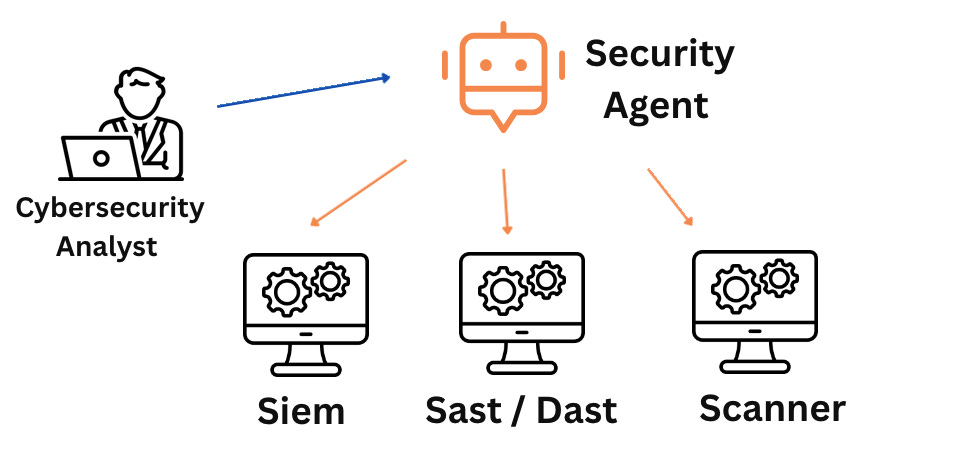
Instead of running 12 different scanners, organizations can now direct a single autonomous agent to continuously find and fix vulnerabilities, contextually and at scale.
2 — AWS Investigative Agent — Incident Response Without Manual Work
This agent:
asks clarifying questions
gathers CloudTrail logs
correlates IAM details
checks EC2 activity
identifies anomalies in cost usage
builds a full attack timeline
produces validated findings
This replaces:
manual IR triage workflows
log investigations
cloud forensics steps
parts of DFIR tooling
The agent does the initial investigation before a human analyst even opens a console.
Why These Announcements Break Existing Cybersecurity Tools
The disruption is not incremental — it is architectural.
Security tools fail under agentic AI because they were never designed for autonomous systems.
Here’s the core problem:
1. Tools expect humans to orchestrate workflows.
Agents orchestrate themselves.
2. Tools return alerts.
Agents return actions.
3. Tools focus on individual checks.
Agents understand context across systems.
4. Tools are expensive to scale.
Agents scale horizontally with minimal cost.
5. Tools assume slow, episodic, human-led processes.
Agents operate continuously and autonomously.
Put simply:
Cybersecurity tools were not designed for systems that investigate themselves
The old paradigm collapses when the investigator is software.
What Will Replace Today’s Security Tools
As agentic AI becomes mainstream, we’re moving toward a new security stack.
Here’s what the next five years will look like.
1. Multi-Agent Security Systems
Security won’t be a set of tools — it will be an ecosystem of cooperating agents:
continuous pen-testing agents
continuous detection agents
continuous incident response agents
continuous compliance agents
Security becomes living software.
2. Autonomous Threat Modeling Agents
Threat modeling will shift from manual workshops to AI agents applying:
STRIDE
MITRE ATT&CK
NIST
cloud architecture context
Continuously.
3. AI-Native SIEM Replacements
Agents will:
consume logs
map causality
detect attack paths
recommend fixes
execute containment
Dashboards are replaced by AI-driven decisions. You might be looking at a dashboard of Agents doing stuff more than alerts !
What Cybersecurity Professionals Must Learn Now
This transition does not remove cybersecurity jobs — it removes cybersecurity tasks.
If your job consists of those tasks, you are at risk.
Here are the skills that will thrive in the agentic era:
Skills That Thrive
AI supervision
Agentic AI security
Threat modeling
Cloud-native architecture
Identity governance
Interpreting agent output
Designing guardrails and oversight
These are high-leverage human skills that AI cannot easily replace.
Skills That Will Fade
manual pen-testing
writing detection rules
manual log correlation
manual code review
static compliance checks
repetitive cloud reviews
SOC Level 1 analysis
These are precisely the tasks AWS has now automated.
The Bottom Line
Agentic AI will break most of today’s cybersecurity tools — not because the tools are bad, but because the assumptions behind them are obsolete.
AWS has shown us the future:
A world where autonomous agents perform security work continuously, intelligently, and at machine speed.
The question for cybersecurity professionals is simple:
Will you learn to supervise these agents — or will you compete with people who do?


Great post!
Do you believe it is really possible to remove humans from the equation?
Strong take on the paradigm shift from tools to agents. The distinction you make between "tools return alerts, agents return actions" cuts through a lot of noise. What's underappreciated is how this flips the economics of security, when an investigative agent can autonomously correlate CloudTrail with EC2 activity patterns, you're not just automating L1 SOC work, you're collapsing the latency between detection andresponse to near-zero. The real battleground will be agent oversight frameworks, becuase autonomous pentesting at scale without proper guardrails is a compliance nightmare waiting to happen.